Posts - Page 2
Mostrando 13-24 de 46 publicaciones
Optimización de Seguridad de Costos en la Nube: CloudHealth vs Turbonomic vs AWS Well-Architected
Domina FinSecOps con estrategias integrales de optimización de seguridad de costos. Compara CloudHealth, Turbonomic y el Marco AWS Well-Architected para la gestión de costos en la nube empresarial mientras mantienes la postura de seguridad.

Enfrentamiento de Herramientas SAST: SonarQube vs Semgrep vs CodeQL en CI/CD
Comparación exhaustiva de herramientas SAST para pipelines de DevSecOps. Analiza el rendimiento, la precisión, las capacidades de integración y la rentabilidad de SonarQube, Semgrep y GitHub CodeQL para la seguridad empresarial en CI/CD.

Automatización de Seguridad Basada en Eventos: Integración de CloudEvents + SIEM
Construya automatización de seguridad empresarial basada en eventos con CloudEvents, Knative e integración SIEM. Aprenda respuesta automática a incidentes, correlación de amenazas y orquestación de seguridad para operaciones de seguridad en tiempo real.
Arquitectura de Confianza Cero para Kubernetes: Malla de Servicios + Políticas de Red
Implementa seguridad de confianza cero empresarial en Kubernetes con malla de servicios Istio, políticas de red Cilium y TLS mutuo. Aprende control de acceso basado en identidad, encriptación de tráfico y microsegmentación para clústeres de producción.
Seguridad de Contenedores a Escala: Desde la Construcción hasta la Ejecución
Estrategia integral de seguridad de contenedores que cubre el escaneo de imágenes con Trivy y Grype, protección en tiempo de ejecución con Falco, seguridad de registros y atestación de la cadena de suministro. Seguridad de contenedores de nivel empresarial para equipos DevSecOps.

Construyendo una canalización CI/CD de confianza cero: del código a la producción
Guía completa de implementación para la seguridad de confianza cero en canalizaciones CI/CD. Aprende a integrar puertas de seguridad, RBAC y atestación de la cadena de suministro con GitHub Actions, GitLab CI y Azure DevOps para automatización de seguridad de nivel empresarial.
IoT Reversión 101: Descubrimiento
Antes de adentrarnos en el mundo de la ingeniería inversa, necesitamos discutir qué es realmente la ingeniería en su con...
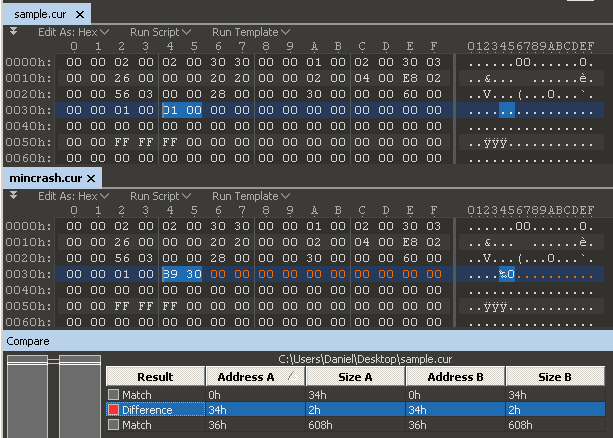
El asombroso mundo del fuzzing de archivos
El mundo del File Fuzzing está lleno de una exhibición verdaderamente espectacular de pruebas. Es el último cambio en la...
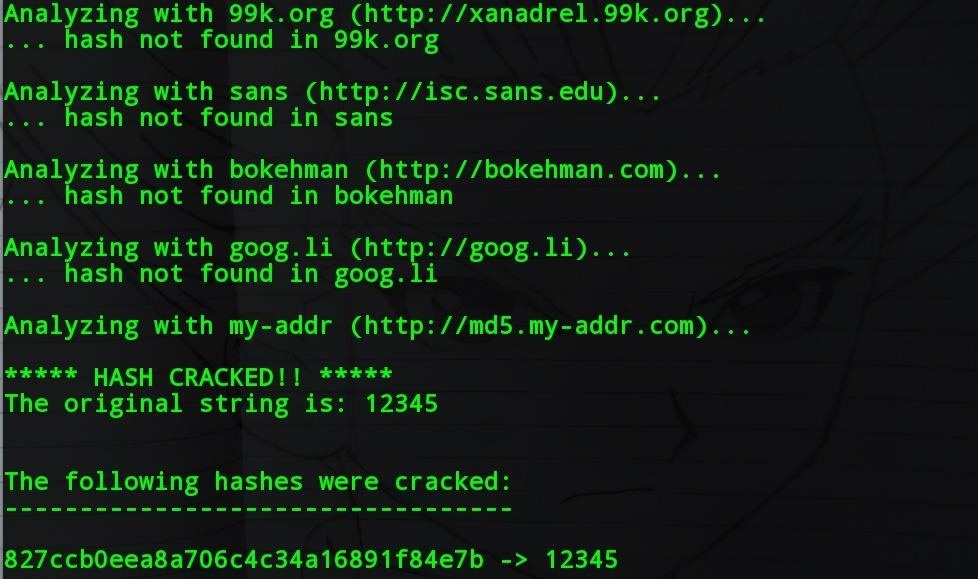
Cracking de Hash Moderno
Cuando se trata de la ruptura de hashes, un programa de ruptura de hashes que funciona con una enorme base de datos de h...

Neverwave: Funcionalidad IDS/IPS en tu navegador con inspección TLS
Durante los últimos años, la tecnología IDS/IPS ha ayudado a detectar actividad maliciosa no solo en el lado del servido...

Pentesting de aplicaciones iOS con OSX y un dispositivo con jailbreak
Hoy explicaremos cómo realizar una evaluación básica de seguridad en una aplicación iOS usando Mac. Para esta evaluación...

Seguridad OT en h-c0n 2020
En los últimos años, los dispositivos OT han estado cada vez más expuestos a internet, los dispositivos IoT se han acerc...