TSM Bible
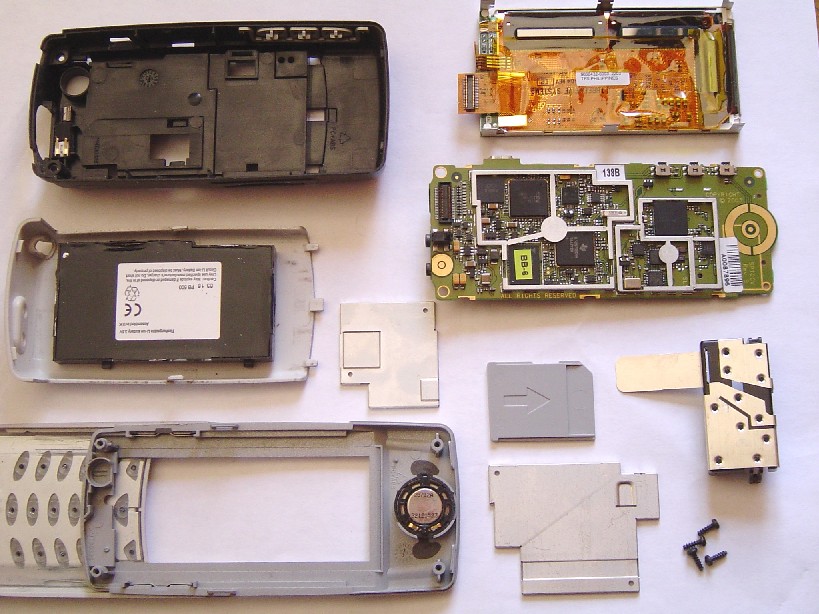
In 2003, the TSM30 mobile phone from Vitelcom hit the market - a mobile with many features developed by a Spanish company at a very reasonable price. Before the TSM30, the TSM100 had been released, a similar phone but with a resistive touch screen.
These mobile phones created a community of users in Spain and very interesting things happened. But what undoubtedly makes this mobile special is that it was the first time that the GSM stack was leaked, as well as the code of a DSP (TI Calypso). This leak is attributed to the ?Hispaphreak group, which posted all the source code on the (then famous) free projects portal Sourceforge. Since no one noticed for so many years, the code immediately came to be considered PUBLIC DOMAIN.
Thanks to this contribution from this group of Spanish hackers, projects like OpenBSC, OpenBTS, OsmocomBB emerged…

TSM30 205 Terminal Features
System
- Operating System: Proprietary
- Storage: 2 MB
- Card: MMC/SD
- J2ME: YES
Screen
- 160x128 pixels, 65k colors
Camera
- 0.3MP (640x480 Pixels)
Other Data
- Calendar: YES
- Vibration: YES
- Radio: NO
- Observations: I-Mode, SD/MMC
- SAR: 0.95 W/kg (head)
Networks
- Band: 2G: GSM 1800, GSM 900, GSM 1900
- GPRS: YES
Battery
- Autonomy (Call): 2.3 h (GSM)
- Autonomy (Standby): 180 h (GSM)
- Battery: Li-Ion
- Removable: YES
Appearance
- Dimensions: 113x48x21 mm
- Weight: 110 gr
- SIM: SIM
Communications
- Bluetooth: NO
- NFC: NO
- IrDA: YES
- USB: YES
- WiFi: NO
- GPS: NO
- Messages: SMS/EMS/MMS
Development Environment
The firmware code is completely written in C. To compile it from the sources, which are available on the Internet, we’ll need to install some Texas Instruments utilities, or download the development environment that only works on NT-compatible systems (Windows NT, 2000, XP, 2003).
Inside the zip, we’ll find not only the firmware source, but also the necessary compilers (TEXAS INSTRUMENTS) to build the firmware.
The code is very well organized and documented. We can find different classified directories. I want to highlight that in the project, objects are compiled for both the MCU (MicroController Unit) and the DSP (Digital Signal Processor). As you can imagine, the operating system runs on the MCU and the Baseband on the DSP.
To mount the units with the compilers, we’ll run the mount.bat file. This will mount 3 units:
- R:
- S:
- W:
We’ll find a file called Official.zip, which contains the actual source code. We’ll need to decompress it (making sure the properties are not read-only) and mount it as V: like this:
subst V: OfficialTo compile the firmware, we just need to go to V:\Common\INTEGRATION\bin and run dmakeall.bat
Internal Prototype Definitions
#if (MODULE_NUMBER == MODULE_PKRN)Communications
The GSM communication routines are in the MCU\Layer1 and MCU\Protocol directories with some definitions in MCU\inc\cdg
The stream structures can be found in spy_decoding.ini
For example, we can see that it supports these values for “Progress indicator information element”:
LOC_USER 0x0 /* user */
LOC_PRIV_NET_LOCAL_USER 0x1 /* private network serving the local user */
LOC_PUB_NET_LOCAL_USER 0x2 /* public network serving the local user */
LOC_TRANSIT_NET 0x3 /* transit network */
LOC_PUB_NET_REMOTE_USER 0x4 /* public network serving the remote user */
LOC_PRIV_NET_REMOTE_USER 0x5 /* private network serving the remote user */
LOC_INTERNATIONAL_NET 0x7 /* international network */
LOC_BEYOND_POINT 0xA /* network beyond interworking point */
LOC_GNOLZ_1 0x1 /* reserved */Which means it does accept the value 0x3, and will treat it with the meaning of “transit network”, although later the program in MCU\Protocol\CC\Src\CC_FFK.C handles it as if it were the same as LOC_PUB_NET_LOCAL_USER. It transforms LOC_TRANSIT_NET into LOC_USER.
Hello World
Well, now that we’ve familiarized ourselves with the mobile’s development environment, let’s do some practice… and… what better than “Hello World”?
We’ll move to the directory V:\MCU\Presentation\Idle\Src and open pidl04debug.hv which contains definitions of debugging utilities. Here we can capture a code entered by keyboard and launch the application we want (our “Hello World”)… and well, since you’re very l33t and hax0rs… we’ll put “##31337” as the access code to our application.
typedef struct {
char * p_KeySeq;
t_pidl_KeyFunction * p_Func;
} st_pidl_KeyTable;
GLOBAL_EXT const st_pidl_KeyTable tabla[]
= {
"##31337", pidl04_nuestra_funcion,
/*
...
...
...
*/
NIL, pidl04_06UnknownSeq
};Now let’s create our function by adding the following lines to pidl04debug.c:
u8 pidl04_nuestra_funcion(char *pp_String)
{
pcom02_11SimpleTimedBox((u8 *)"Hola Mundo", (u8 *)"l33t Msg", PPMT_EOL_DUMMY_PROMPT_SPT2, PPMT_EOL_DUMMY_PROMPT_SPT2, 0 );
return (TRUE);
}The user interfaces for confirmation are defined in V:\MCU\Presentation\Common\Src\pcom02cfirm.c:
void pcom02_01EasySettingMessageBox( st_MsgBoxPZ *pl_MsgBox );
u16 pcom02_09SimpleMsgBox( u8* p_Text, u8* p_Title, t_PromptId v_Text, t_PromptId v_Title, u32 v_Flags );
u16 pcom02_10SimpleBox( u8* p_Text, u8* p_Title, t_PromptId v_Text, t_PromptId v_Title, u32 v_Clear );
u16 pcom02_11SimpleTimedBox( u8* p_Text, u8* p_Title, t_PromptId v_Text, t_PromptId v_Title, u32 v_Clear );
u16 pcom02_12SimpleYesNoBox( u8* p_Text, u8* p_Title, t_PromptId v_Text, t_PromptId v_Title, u32 v_Clear );
u16 pcom02_13SimpleInfoBox( u8* p_Text, u8* p_Title, t_PromptId v_Text, t_PromptId v_Title, u32 v_Clear );
u16 pcom02_14SimpleWarningBox( u8* p_Text, u8* p_Title, t_PromptId v_Text, t_PromptId v_Title, u32 v_Clear );
u16 pcom02_15SimpleYesNoCancelBox( u8* p_Text, u8* p_Title, t_PromptId v_Text, t_PromptId v_Title, u32 v_Clear );
u16 pcom02_16SpecialTimedBox( u8* p_Text, u8* p_Title, t_PromptId v_Text, t_PromptId v_Title, u32 v_Clear, u8 vp_DisplayAttributes );
u16 pcom02_17SimpleGoPostponeDeleteBox( u8* p_Text, u8* p_Title, t_PromptId v_Text, t_PromptId v_Title, u32 v_Clear );
u16 pcom02_18SimpleSilentBox( u8* p_Text, u8* p_Title, t_PromptId v_Text, t_PromptId v_Title, u32 v_Clear );
u16 pcom02_19SimpleSilentTimedBox( u8* p_Text, u8* p_Title, t_PromptId v_Text, t_PromptId v_Title, u32 v_Flags ) ;
u16 pcom02_20SimpleBoxGo( u8* p_Text, u8* p_Title, t_PromptId v_Text, t_PromptId v_Title, u32 v_Flags, st_MsgBoxPZ *pl_MsgBox );
u16 pcom02_23SimpleIconTimedBox ( u8* p_Text, u8* p_Title, t_PromptId v_Text, t_PromptId v_Title, t_IconId v_Icon, u32 v_Flags );
u16 pcom02_24SimpleBoxWarm( u8* p_Text, u8* p_Title, t_PromptId v_Text, t_PromptId v_Title, u32 v_Flags );
u16 pcom02_26ExitAndDiscardNotif( void );
u16 pcom02_27DeleteConfirmation( void );
u16 pcom02_99MsgBoxTest( u8* p_Text, u8* p_Title, u8* p_But );
u16 pcom02_25OneButton( u8* p_Text, u8* p_Title, t_PromptId v_Text, t_PromptId v_Title, u32 v_Flags );
u16 pcom02_26ExitAndDiscardNotif(void);
u16 pcom02_27DeleteConfirmation(void);
u16 pcom02_28DeleteAllConfirmation(void);
u16 pcom02_29PleasePowerCycle(void);
u16 pcom02_30FileSystemFull(void);
u16 pcom02_31MemoryCheckAndNotify(u8 * pp_Level, u8 * pp_Percentage);If we want to work with buffers that the user copies and wants to paste, we’ll use the following functions:
_globext_ u8 pcom03_01Copy ( t_BufferType vp_BufferType, void *vp_Data, u16 vp_Size );_globext_ t_BufferType pcom03_02Paste ( void **pp_DataPtr, u16 *pp_SizePtr );_globext_ void pcom03_03InitialiseClipboard ( void );_globext_ t_BufferType pcom03_04IsBufferData ( void );_globext_ u8 pcom03_05IsBufferLocked ( void );_globext_ void pcom03_06LockBuffer ( void );_globext_ void pcom03_07UnlockBuffer ( void );_globext_ u8 pcom03_08CanCopy ( u8 a, u16 b, st_HandlerControlBlock *c );_globext_ void pcom03_09LaunchTimeoutTimer ( t_TimeoutContext ) ;_globext_ void pcom03_10StopTimeoutTimer ( t_TimeoutContext ) ;
GSM/GPRS/I-MODE Introduction
Every time we turn on a mobile phone, we’re presented with an invitation (CHV1) on the screen to enter the PIN1 that will allow us to enter the GSM network. This Personal Identification Number doesn’t need the mobile telephone network, but its validation is done by the SIM card itself.
To do other things like changing options once we’re connected to the network (CHV2), we’ll need to use PIN2, but it’s not necessary to know it for normal use on the network.
The network access process is initiated by the mobile once the user has entered the PIN correctly; at that moment, the mobile receives the RAND from the network, which is a random number (RANDOM) that it uses along with the Ki to generate SRES and Kc keys.
The Ki (Internal Key) is a number stored in the SIM that cannot be directly accessed from the mobile terminal, however operators have a database with the Ki’s in the AC (Authentication Center).
The SRES (Result) is returned to the network to complete the authentication system and is generated with the Ki and the RAND.
The Kc (ciphering key) is generated with the A3 algorithm, and will serve us as a key to encrypt communications when the network has encryption active. Like the SRES, the Kc is generated with the Ki and the RAND. On 11M, many mobile phones from the MoviStar company warned that no type of encryption was being used for reasons that we can all imagine.
The IMSI (Mobile Subscriber Identification Number) is a number that identifies us worldwide as subscribers to a mobile telephone operator’s network. It consists of MCC, MNC, and MSIN.
MCC (mobile country code) is the identifier of a country’s network and consists of 3 digits. MNC (mobile network code) is the identifier of an operator’s network, formed from 2 digits. MSIN (mobile subscriber identification number) is the subscriber’s identification number (it doesn’t have to coincide with the MSISDN, that is, the subscriber’s phone number that the network assigns us when it has verified the data), and 10 digits are reserved for it.
Most mobile phones look at the first 3 digits of the IMSI (which indicate the country) to display menus in one language or another.
The TMSI is the time that a location update must execute to inform the network of the availability of our mobile terminal.